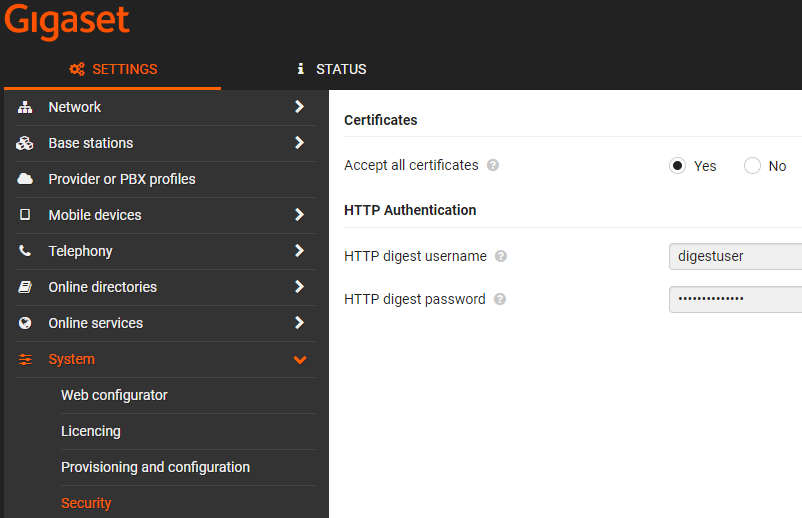
From software 2.53 or higher it is possible to add the HTTP digest credentials via the Gigaset Redirect server. If the customer provisioning server has an HTTP digest security implemented, it allows you to add the HTTP digest credentials via the redirect server so that zero touch provisioning is working.
@startuml
!pragma teoz true
participant "ein2" as ein2
participant "Gigaset Redirect server" as redir
participant "Customer provisioning server" as provserv
ein2 -> redir: Connect to Gigaset redirect server
redir -[#red]> ein2: 401 unauthorized
ein2 -> redir: Connect to Gigaset redirect server with: Username = MAC address and Password = stored in device
redir -> ein2: Customer Provisioning server URL with http digest username and password
ein2 -> provserv: Connect to Customer provisioning server
provserv -[#red]> ein2: 401 unauthorized
ein2 -> provserv: Connect to Customer provisioning server with: Username = MAC address and Password = stored in device
provserv -[#red]> ein2: 401 unauthorized
ein2 -> provserv: Connect to Customer provisioning server with: Username = http digest username and Password = http digest password
provserv -> ein2: Provisioning file
note over ein2
If provisioning file download was successful
then HTTP digest credentials are stored in the
device and visible in the web-interface
end note
@enduml |
Redirect server URL format = http(s)://<username>:<password>@URL 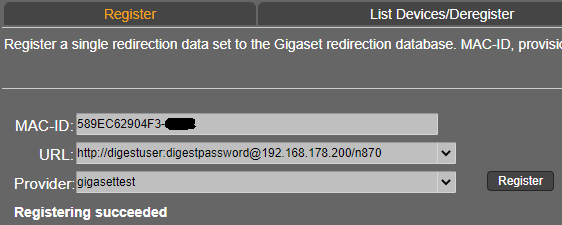
| 
