|
We as Gigaset deliver an factory installed client certificate that can be used to integrate the device into the customer network. We as Gigaset do not take for the full live-cycle, responsibility for the client certificate security. The factory installed client certificate can be used for onboarding the device in the customer network. If more security is required, you can create your own client certificate and authorization authority. The certificate can be updated via auto-provisioning and the web-interface. Client certificate history:
|
Default, Factory installed Client certificates are pre-installed on the device. The Factory installed Client certificates can be found here:
How to check the CN: There are 2 types of client certificates possible:
The correct client certificate will have CN = <MAC address> You can the check the CN using the following openssl command. You can execute this on the Nx70 (CLI access) or on external Linux PC, replace IP address with the IP address of your DECT device)
|
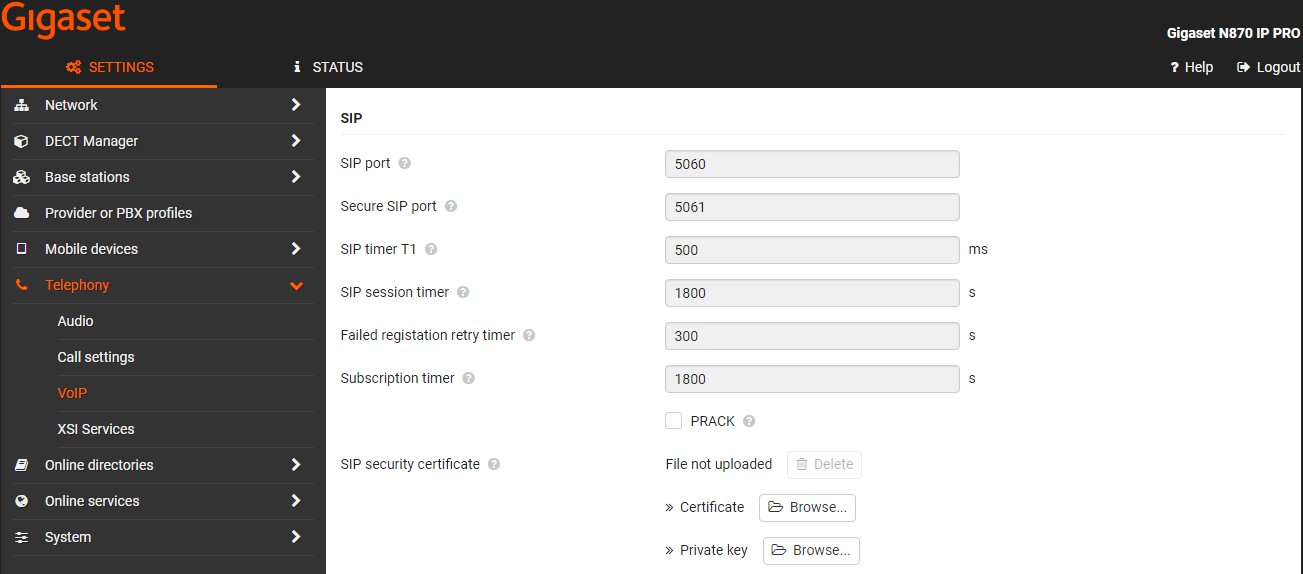
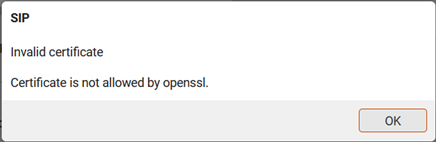
The Client certificates can be uploaded from the web-interface, go to: SETTINGS - Telephony - VoIP.
|
<?xml version="1.0" encoding="UTF-8"?> <firmware> </firmware> <nvm> </nvm> <custom> <step type="certificate" url="<URL to certificate>" key="<URL to Private key>" flags="CLIENT_CERT" /> </custom> </provisioning> |
You can generate your own Client certificates using a Linux machine. To create self-signed client certificate you have to follow the instructions below. If you have own CA you can skip the first step.
and follow the on-screen instructions.
3. To check the content of the certificate:
As Common Name you can put the MAC address of the device (with capital letters). You can download the N870.crt and N870_key.pem file using WinSCP. Go to: SETTINGS - Telephony - VoIP to upload N870.crt and N870_key.pem files.
|